- On Sep 6, 2023 2:54:07 PM
- by: Joe Rudolph
- 25 minutes Read
Since COVID-19, the Federal Bureau of Investigations (FBI) has seen a 300% increase in cybercrime. Along with this risk increase, leaders are also grappling with a massive change in technology over the last decade. Even in the last few years, how modern businesses and organizations work has changed drastically.
With new digital innovations and the rise of remote working, there are many new opportunities for bad actors to get into your network or steal your organization’s data. However, it’s not always clear to leaders or their employees how new technology, applications, or processes create vulnerabilities.
To help answer your questions and secure your data, we created this FAQ-styled guide on the basics of cybersecurity. Below, we get you up to speed on the latest cybersecurity basic terminology, common mistakes we see, the core pillars of building a strong security posture, and more.
If you’re looking for something specific, click on one of the chapter headers below.
- What are the 3 Core Pillars of Cybersecurity?
- What Basic Cybersecurity Terms Should I be Familiar With?
- What is the Origin of Modern Cybersecurity Practices?
- What Mistakes Should Your Organization Avoid?
- Why are Your Employees Your Biggest Cybersecurity Risk?
- What Common Cybersecurity Risks Do Small Businesses Face?
- What IT Security Risks do Pittsburgh Businesses Need to Know?
- What is a Good Microsoft Security Score?
- What Steps Should be Taken to Remediate Cybersecurity Risk?
- What Tips Can Help Your Business Prevent Scams?
- Why is Cybersecurity Awareness Training Important?
- Who Needs Cybersecurity Insurance?
- Why are Cyber Attacks More Common During the Holidays?
- What Cybersecurity Best Practices Should Small Businesses Follow?
- What are the Benefits of Multi-Factor Authentication?
- What is the Difference Between Reactive and Proactive Computer Security?
- What Cybersecurity Services are Available in Pittsburgh?
- How Can I Choose the Right Cybersecurity Partner?
|
Want a cybersecurity resource written by experts to read on the go? |
 |
1. What are the 3 Core Pillars of Cybersecurity?
When it comes to cybersecurity, there are three core pillars that organizations need to use as a guiding post – and thatour team at Ceeva focuses on for our clients. By understanding what is at stake, your employees can help support your cybersecurity plan day-to-day.
1. Security
First and foremost, cybersecurity measures are about security. Protecting company data, the identity of a company’s employees, and the personal data of its customers is what cybersecurity is all about. Training to avoid phishing scams and how to identify and protect sensitive data is just the starting point.
The entire sum ofcybersecurity best practices is designed to provide a secure exchange of information to conduct necessary activities without compromising your data.
A solidcybersecurity plan that protects sensitive data and confidentiality also builds trust, enabling your clients to share their personal details more willingly.
2. Confidentiality
The second pillar of cybersecurity is confidentiality. In some industries, confidentiality is a legal requirement, and in others is just a good business practice. Either way, ensuring that your organization’s data remains protected and isn’t shared with or exploited by third parties is the goal of cybersecurity measures.
3. Trust
The third pillar of cybersecurity is trust. Individuals pay attention to how their data is handled when they do business or work with an organization. Something as menial as giving personal information to one company and then receiving advertisements from another can be enough to affect the trust in your employee or client relationship.
2. What Basic Cybersecurity Terms Should I Know?
Cybersecurity Ventures Magazine expects global cybercrime costs to reach$10.5 trillion annually by 2025! To avoid these high costs, it’s vital to make sure you and your employees know basic cybersecurity terms.
But with terms like virtual private networks (VPN), malware, domains, andthe cloud floating around, talking about cybersecurity can sometimes feel like a foreign language. Here’s a quick refresher on how IMB defines cybersecurity:
Cybersecurity is the practice of protecting critical systems and sensitive information from digital attacks. Also known as information technology (IT) security, cybersecurity measures are designed to combat threats against networked systems and applications, whether those threats originate from inside or outside of an organization.
Why is this important to know? Before you can understand your needs, you first need to understand what your IT team ormanaged service provider is talking about.
If you want to understand the latest basic cybersecurity terms,read this article. Inside, you’ll learn nine commonly used terms by IT experts, and understand exactly how they relate to cyber attacks.
3. Where do Modern Cybersecurity Practices Come From?
Cybersecurity has been around as long as the world wide web has been in existence. It is the orchestrated efforts to proactively mitigate risk and remediate breaches that compromise network data.
“We’ve been talking about cybersecurity for years. But the problem is still there, it’s always changing.” - Jerry Shafran, CEO of Ceeva Via Event: Don’t Gamble on Your Cybersecurity: Reduce Risk and Manage Your Insurance Premiums
OnApril 30, 1993, the first web browser became publicly available, and by the beginning of 1994, early forms of firewalls and other security measures began to emerge. From there, the evolution of technology has both expanded in opportunity and complexity. This has fueled a need for more capable cybersecurity solutions.
As we look at theorigin of cybersecurity and the future of IT services, these two fields are becoming more closely intertwined. As a result, managed services providers are stepping up to fill the need for bothco-managed IT and outsourced cybersecurity.
4. What are Common Cybersecurity Mistakes You Should Avoid?
In many cases, breaches occur because there isn’t someone doing enough to stop or prevent them. Especially in smaller companies, the burden of maintaining technology seems to fall on administrative staff rather than experienced IT professionals.
Between a lack of up-to-date knowledge and time to give basic cybersecurity measures enough attention, these organizations are unwittingly letting their guard down. Did you know that breaches most often occur as the result of out-of-date software, lax security protocols, or well-meaning employees?
In this article, you will learn how to strengthen your security posture by avoiding thesecommon cybersecurity mistakes. We’ll show you how to implement an effective security policy and address common housekeeping items that are likely putting your organization at risk.
There’s a reason why94% of our clients continually renew our managed cybersecurity services in Pittsburgh! We cover these cybersecurity basics before a costly breach occurs.
5. Why are Your Employees Your Biggest Security Risk?
An organization’s biggest risk is also their first line of defense.
The difference is in how you approach cybersecurity within your team. Every employee with network access, including customer service team members and operational staff, all have the ability to help or hurt your organization’s security.
“In my years of experience, the end-user is the #1 way a company becomes compromised.” - Joe Rudolph, Privacy and Security Officer atCeeva
With61% of small businesses not having the resources to match cybersecurity efforts in larger corporations, this can lead to disastrous effects.
Phishing emails, mobile network access, and poor data practices all create a perfect storm putting your employees at the point of failure for big, consequential data breaches. Keep track of thecybersecurity risks that your employees pose and how you can effectively turn those risks into safeguards.
6. What Cybersecurity Risks Do Small Businesses Face?
Speaking of risks, how likely is it that a small business will suffer a ransomware attack or fall victim to a social engineering scheme? Small businesses may be three times more likely to be on the receiving end of an attack.
Why? It’s simple – small businesses have fewer resources, making them easier targets for hackers. Here’s a quick overview of thecybersecurity risks you face in your day to day:
- Ransomware can restrict access to your vital data.
- Phishing attacks draw out personal information, deceiving companies into disclosing credit card data or other sensitive details.
- Social engineering attacks range from simple deception to complex schemes filled with fake employees trying to gain access to your systems.
Make sure to take the time to learn about these cybersecurity risks, or ask anIT expert, to better protect your small business from a cyber attack!
7. What IT Security Risks do Pittsburgh Business Owners Need to Know About?
“Cybersecurity is a big concern. We just went through cyber liability insurance which was really challenging. I see the horror stories from the law journals and fraud in title insurance journals. But if you have a good IT partner you don’t have to think about this, they’re coming up with ideas to address your cybersecurity and systems issues. In the past 15 years, IT has become a major component of our business." - John Prorok, Partner at Maiello Brungo & Maiello, LLP Law Practice, Pittsburgh
Pittsburgh is a bustling metropolis with just over 300K residents and hundreds of businesses of all sizes. Pittsburgh is a hub of innovation and technology, and that means it’s a magnet for those looking to exploit technology.
For businesses, this means heightened IT security risk. It’s imperative that business owners proactively evaluate their security position and continuously improve their defenses.
To evaluate your current IT state, leaders can:
- Review and assess existing cybersecurity policies (or make them!).
- Audit, update, and test your hardware and software.
- Implement data backup systems and disaster recovery plans.
Wish you had a handbook to give you actionable direction against cyber crime? Download our free cybersecurity handbook today!
One step that Pittsburgh business owners can take today is to partner with an IT Managed Services Provider (MSP). A team like Ceeva can help your business understand and address unique cybersecurity risk factors today, beginning with your Microsoft Security Score.
8. What is a Good Microsoft Security Score?
More thanone million organizations use and trust Microsoft to provide a common language that everyone can understand.Microsoft’s Security Score is a universal metric that many businesses use to quickly assess how well – or not well – they are managing cybersecurity.

Specifically, this score is an important metric when communicating with cybersecurity insurance providers. This one score can tell insurance companies if your organization is following cybersecurity best practices like the use of multi-factor authentication, restrictive access protocols, and virtual private network (VPN) access.
As55% of businesses haven’t set up multi-factor authentication yet, this score can be a rude awakening.
Generally speaking, a good Microsoft Security Score is between 80-100%, while scores below 50% are generally considered deficient. More importantly, monitoring this score demonstrates a commitment to proactive cybersecurity management, which translates to effective risk management and potentially lower insurance premiums.
9. What Steps Should Be Taken to Remediate a Cybersecurity Vulnerability?
Cybersecurity remediation is the process of taking action to identify and neutralize a security threat. While your business should aim to prevent incidents, it’s equally important to have the right course of action when a breach inevitably occurs.
“Hackers are getting smarter and more creative about how they get into networks and inflict damage. The old ways of protecting data and infrastructure – antivirus, annual cybersecurity training for employees, reactive fixes – aren’t cutting it for a lot of organizations now.” - Rick Topping, Ceeva Vice President of Operations
How you identify and prioritize threats can make the difference between effective cybersecurity management and a serious drain on financial resources. This means that you will need to decide what your acceptable risk threshold is, how you will concentrate your resources to identify, and address vulnerabilities.
Followthese steps to create a tailored cybersecurity plan based on your unique results.
10. What is the Best Way to Prevent a Cybersecurity Scam?
Did you know that phishing and social engineering attacks start out as unsuspecting emails or phone calls?
You might encounter a caller posing as an employee from a reputable company in order to gain your trust. Or, you might find that the person on the other end of an email becomes pushy when asking for sensitive information.
These are all tactics designed to facilitate deception. The best way to prevent a cybersecurity scam is to know what to look out for. At Ceeva, we recommend proactive employee awareness training as part of a culture of security to keep everyone on top of current trends, like:
- Watch for spoofed phone numbers
- Practice healthy skepticism
- Use multiple means to verify contact identity
11. Why is Cybersecurity Awareness Training Important?
Cybersecurity is an all-hands-on-deck effort. This means that any employee with access to company technology needs to be aware of the inherent dangers, including how cyberattacks happen and what they can do to prevent them.
That’s the goal ofcybersecurity awareness training. It should be provided during onboarding for all new employees, with a refresher at least once annually or as often as needed. This training should include topics like:
- Passwords
- Access protocols
- Clicking links
- Downloading files
- Opening emails
Cybersecurity awareness training can be an important first step in preventing your next breach. Make the most out of your efforts with outsourced training programs designed and taught by cybersecurity professionals. It might even be a requirement for obtaining cybersecurity insurance.
12. Who Needs Cybersecurity Insurance?
Cybersecurity insurance is a special type of business policy designed to help cover losses incurred as a result of a cyber incident.
While that’s lower than some of the eye-popping sums faced by larger companies, it’s enough to put many out of business. For small businesses, a goodcybersecurity insurance policy can:
- Cover legal expenses
- Fund recovery efforts
- Insulate from operational losses
- Supplement your security measures
In 2023, nearly every business uses technology. The need for cybersecurity insurance is no longer limited to big tech companies. If you are utilizing a customer relationship management (CRM) or enterprise resource management (ERM) software, it’s time to evaluate your coverage needs.
Change in Cyber Insurance Premiums, 2017-2020: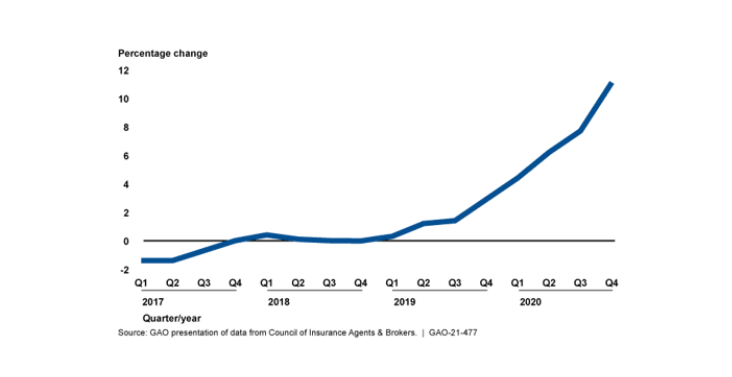 Source:Government of Accountability Office: Rising Cyberthreats Increase Cyber Insurance Premiums While Reducing Availability
Source:Government of Accountability Office: Rising Cyberthreats Increase Cyber Insurance Premiums While Reducing Availability
13. Are Cyber Attacks More Common During the Holidays?
Major retailers like Target and entertainment companies like EA Games have experienced high-profileholiday cyber attacks. And it’s no coincidence that these incidents popped up during the busiest retail season of the year.
During the Christmas holiday season, which begins the day after Thanksgiving and extends through the end of the calendar year, more people are spending on gifts. The uptick in volume, paired with the lack of familiarity with some of the products and providers, creates opportunity for hackers.
This opportunity fuels an increase in cyber incidents during theholiday season. And for businesses that are not directly connected to the gift-giving festivities, hackers are lying in wait for your employees to be distracted and out of the office for prolonged periods of time while they play in your files.
Pro IT Tip: Do not allow employees to access company resources from an open or free Wi-Fi connection.
14. What Best Practices Should Small Businesses Follow?
With all the risk, you might be asking yourself – where should I start?
There is a lot of ground to cover, and if you have limited resources, you want to know that you are spending them effectively. If our team had to pair it down to just threecybersecurity best practices, we advise leaders focus on:
- Routine cybersecurity awareness training
- Business continuity & disaster recovery planning
- Routine data backups
Training arms your first line of defense with the right information. A business continuity and disaster recovery plan ensures that you know what to do next when trouble strikes. And routine backups ensure that you have access to clean, uncompromised data when you need it.
Next, take a look at the specific cybersecurity measures you can implement right now:
15. What are the Benefits of Multi-Factor Authentication?
Multi-factor authentication involves requiring two or more identifiers to verify a user's identity. Thebenefits of multi-factor authentication (MFA) helps protect the integrity of user credentials. This might look like entering a self-selected password and then verifying a pin code received on a second device.
In more secure environments,MFA Protocols might include biometrics like fingerprints or facial recognition along with a pin number or password. The use of multi-factor or two-factor authentication protocols is part of a zero-trust approach to cybersecurity that recognizes your best employees are also inadvertently some of your weakest links.
Gain total confidence in your cybersecurity posture with our Ceeva Shield Offering! Learn how this can help your team below:

Overview of services and tools included in each Ceeva Shield package.
Download a summary of Ceeva Shield.
This small step is a good way to ensure systems access restrictions work as they are intended. In addition to implementing MFA, you might also consider written policies outlining progressive disciplinary action for password sharing or leaving computers logged in, which directly impede the restrictive access measures that support these security initiatives.
Multifactor authentication is just the first step in a move towards more proactive cybersecurity management.
16. What is the Difference Between Proactive and Reactive Security?
Do you only focus on cybersecurity when something happens? If your systems security is on the back burner until you discover a breach or find an error, that’s reactive. Of course, having protocols in place that identify the next steps during an incident are important, but your security shouldn’t stop there.
Proactive security involves taking steps like providing routine awareness training or conducting penetration testing assessments to find vulnerabilities designed to strengthen your security efforts before there is a problem.
So, what’s the difference betweenproactive and reactive security? It largely lies with what triggers the activity. Proactive security is preventative, while reactive security is remediation focused. Ideally, your cybersecurity plan should include elements of both.
17. What Cybersecurity Services are Available in Pittsburgh?
To keep up with the constant change, an increasing number of businesses andnonprofits are choosing tooutsource IT functions to managed services providers.
Under that umbrella, there are a few different service offerings. Some providers specialize in one or more areas, while others provide a full-spectrum solution. Common cybersecurity services include:
- Application security
- Network security
- End-User security
According to a global outsourcing survey by Deloitte,76% outsource IT functions for their businesses, including both small and large companies. If you’re considering finding a partner to bolster your cybersecurity efforts, you’re not alone.
18. How Can I Choose the Right Cybersecurity Partner?
With the demand for cybersecurity solutions on the rise, the market is full of options. The only question is, how can you be sure that you are choosing the rightMSP partner to meet your cybersecurity needs?
We recommend that you take some time to evaluate the quality and integrity of the company, separate from their expertise. This means asking questions about what they do and who is on their team is equally as important as finding out if they practice what they preach with strong internal security protocols.
Finally, once you have found a provider that has the experience and expertise to meet your needs, the final questions are more about strategic fit. Don’t forget to find out about onboarding, communication, and incident response provisions before you sign on the dotted line.
Get the Expertise You Need with Ceeva’s Managed Cybersecurity Services
The ins and outs of cybersecurity can be complex. With the changing nature of technology creating more intense needs for security, outsourcing to a managed services provider is a smart strategic move. The right provider can help you assess your current state and plan for improvements that will strengthen your security in the future.
In this FAQ guide, we’ve covered a number of cybersecurity best practices, tips, andsolutions to common challenges that you might face. The biggest takeaway is this:
A proactive cybersecurity plan is the backbone of an organization. It should include regularly updating software and systems, implementing multi-factor authentication, adopting a zero-trust model, utilizing best-in class managed detection and response systems, and regularly backing up data.
Unsure where to start? Ceeva can help you strengthen your security one step at a time.
Reach out to our team and learn more about what it’s like to partner with Ceeva.Contact us today to learn more about our managed cybersecurity services.
Subscribe blog for latest updates
By submitting this you will be receiving our latest updates on post.
